Feb 19, 2016
Did you know that PowerShell straight out of the box can have not 1 but 8 different profiles (at last count)! These profiles are a feature of the hosting applications – e.g. the PowerShell Console or PowerShell ISE – and not the underlying PowerShell engine. Other third party hosts may or may not have their own profiles as well.
Each profile is a PowerShell script containing any cmdlets you wish and allows that shell’s environment to be configured to suit the user. Profile scripts can be used to define such things as aliases and\or variables, colours and fonts, set default file directory paths and to pre-load modules. These profiles are run automatically when the PowerShell host application is first started, except when you are using PowerShell Remoting – no profile scripts are run by default on remote computers.
No profile script is created by default, but the PowerShell console and the PowerShell ISE are each capable of having up to 4 profiles each. The 8 profile scripts are listed in the following table, and if there is more than one, then they are executed in the order listed in the table. Note that the directory paths listed also may not exist, and may need to be created when you are creating the profile script itself.
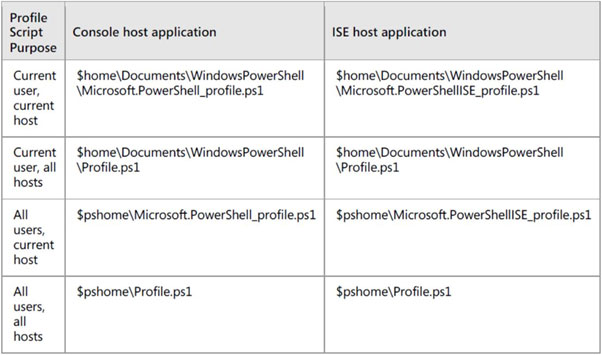
Note that in the above table, $home refers to your user account home folder, for example C:\Users\Administrator. The Documents folder may be My Documents on older versions of the Windows operating system. $pshome refers to the Windows PowerShell installation folder, for example C:\Windows\System32\WindowsPowerShell\v1.0.
Security Awareness
Because these profile scripts are in essence simple plain text files, and if they do exist they typically exist in your Documents folder, makes them vulnerable to malware attacks – especially if you are running the host application using elevated permissions. In that case any malware changes (or malware creation of new scripts) will also be running under those elevated permissions as well. Therefore, it is even more imperative that you are running not only up-to-date antivirus software, but you are also running up-to-date anti-malware software as well – on ALL your Windows PC’s, because all of the currently supported editions of Windows have some version of PowerShell already installed.
There are a couple of things you can do to try to alleviate malware attacks – such as using the AllSigned PowerShell execution policy (requiring all PowerShell scripts to be digitally signed), or having a separate user account (and hence different profile scripts) when running the PowerShell hosts (e.g. logged in user of fsmith and a user account used just for the PowerShell hosts of Adminfsmith), but both of these are rather fiddly and cumbersome, and neither of these are to be considered foolproof. Again, keeping malware of your PC (particularly Administration PC’s) in the first place is your best defence. Malware protection is your responsibility, not PowerShell's.
So go ahead and create your own profiles to make your lives easier to begin with – after all PowerShell is all about automation isn’t it? Just make sure your protection is up to date as well!
How do your Excel skills stack up?
Test NowNext up:
- Transparent Images in PowerPoint 2013
- Configuring Lync Room System
- Rugby in the workplace
- InDesign - Data Import Feature
- Streaming Xbox One to Windows 10
- 3 Simple Pie Chart Tricks
- Tips and Tricks with Nintex Forms
- The Agreement Frame: Solving Complex Arguments
- How-To Series: Photoshop CC Intelligent Upsampling
- My thoughts on the Moto 360 SmartWatch
Previously
- Get a Better View – Through Office Lens
- The problem with accepting constructive feedback
- Adding videos to your website
- The magic of scrollbar control in Excel
- Service Design in ITIL®
- Slugging it out, and the need to bleed
- Remember Me? In one way I hope not!
- Configuring an internet facing deployment for Microsoft CRM Server
- Custom number formats in Excel
- A big flop that broke the rules and broke the records